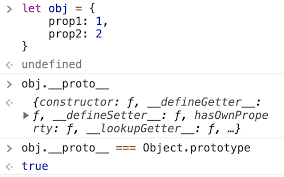
Prototype pollution is a vulnerability where an attacker is able to modify Object.prototype. Because nearly all objects in JavaScript are instances of Object, a typical object inherits properties (including methods) from Object.prototype. Changing Object.prototype can result in a wide range of issues, sometimes even resulting in remote code execution.
which contains basic functionalities such as toString, constructor and hasOwnProperty.
Here’s a simple example of how prototype pollution works.
Steps to reproduce the Prototype pollution attack
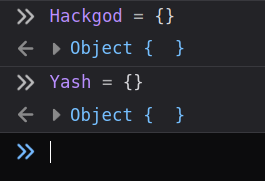
- First make 2 or more empty objects just like shown below.
- Since they are empty objects so they don't have any actions's or commands defined.
- This is the Cruical point because this is the line that cause prototype pollution and overwrites all the previous variables.
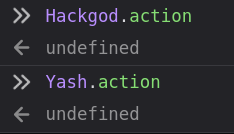
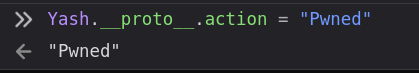
- let's define "Pwned" as valus in Yash object's action using __proto___ function.
Why __Proto__?
__proto__ is a way to inherit properties from an object in JavaScript. prototype is an accessor property that exposes the [[Prototype]] of the object through which it is accessed
- Denial of Service – by triggering JavaScript exceptions
- Remote Code Execution – by tampering with the application source code to force the code path that the attacker injects
- XSS (Cross site scripting).
It overwrites the previous object's or variable's with "Pwned" as action set to Yash's object
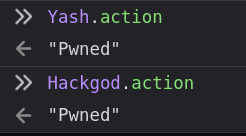
This is how Prototype Pollution works in JavaScript..
Key attack vectors for prototype pollution include user input fields and query parameters passed on to websites. If a site’s JavaScript code iterates through query parameters without sanitizing them, then it might end up running commands that change the object prototype.
Prototype Pollution attack vector's:
- GadgetsWappalyzer-Plugin, Fingerprint.js
- Spinning up the Remote code execution(RCE)AST Injection, Prototype Pollution to RCE
Prototype pollution attack in NodeJS application
Prevention from Prototype Pollution
- Object.FreezeObject.freeze will mitigate almost all cases. Freezing an Object prevents new Prototypes from being added to it.
- Schema validationUsing schema validation to ensure that the JSON data contains the expected attributes. This will remove __proto__ if it appears in the JSON.
- Map primitiveUsing map primitive, which was introduced in the EcmaScript 6 standard, and is now well-supported in the NodeJS environment.
- Object.create(null)Objects created using the Object.create(null) function won't have the__proto__ attribute.
- recursive merge function'spay attention when using recursive merge functions, since they are more prone to Prototype Pollution vulnerabilities than other functions.